The Invisible Engine Securing Your External Attack Surface
ThreatNG automates the complex, foundational work of digital risk discovery and validation. Stop managing disjointed dashboards, eliminate the noise of false positives, and secure your enterprise with an all-in-one External Attack Surface Management (EASM), Digital Risk Protection (DRP), and Security Ratings platform.
What is ThreatNG?
ThreatNG is an agentless, all-in-one cybersecurity platform providing External Attack Surface Management (EASM), Digital Risk Protection (DRP), and Security Ratings. Using purely external, unauthenticated discovery, ThreatNG continuously maps an organization's digital footprint, identifies vulnerabilities, monitors dark web exposure, and delivers prioritized, legal-grade attribution without requiring internal API integrations or agents. The result is immediate justification for enforcing MFA, EDR, and hyper-focused security awareness training only on the specific, highest-risk users the adversary has already selected. The emotional payoff is professional Confidence and quantifiable defense efficacy.
How does ThreatNG solve the Contextual Certainty Deficit?
ThreatNG uses a patented Context Engine™ and multi-source data fusion to eliminate false positives and alert fatigue. Instead of generating lists of isolated assets, the platform iteratively correlates technical security findings, such as open cloud buckets or exposed APIs with legal, financial, and operational data, providing security teams with irrefutable evidence and targeted remediation paths.
Break the "Connector Trap": Purely External, Agentless Mastery
ThreatNG is a purely external, agentless platform that requires zero API keys, internal credentials, or software agents to operate. By breaking the "Connector Trap," ThreatNG performs unauthenticated discovery across your entire digital footprint using only a domain name, ensuring zero operational friction.
Traditional cybersecurity tools force your team into a "Connector Trap," demanding a labyrinth of disparate API keys, internal agents, and complex permissions for every environment you believe you own. This administrative nightmare not only drains your IT resources but leaves you completely blind to the unsanctioned shadow IT, orphaned assets, and rogue third-party exposures that make up the hidden majority of your attack surface. ThreatNG’s one-of-a-kind methodology is entirely connectorless. Operating seamlessly from the outside in, we perform purely external, unauthenticated discovery and assessment across your entire digital ecosystem, encompassing your attack surface, deep/dark web presence, brand protection vectors, and third-party risk profiles. Because it never touches your internal production systems or user devices, ThreatNG introduces zero performance drag and zero friction for your business units. Fully tunable to your specific risk appetite via the DarcRadar™ policy engine, this non-impactful approach illuminates the "unknown unknowns" exactly as an adversary sees them. The result is absolute liberation from deployment headaches, delivering the irrefutable evidence of due diligence you need to restore authority across your borderless digital frontier.
A Unified Platform for Comprehensive Digital Resilience
The ThreatNG ecosystem consolidates three critical cybersecurity disciplines into a singular, frictionless workflow, effectively eliminating the financial and operational burden of maintaining separate, siloed vendor contracts.
Operating as a continuous scout outside the organizational perimeter, the platform performs unauthenticated discovery of all internet-facing assets. It identifies shadow IT, orphaned subdomains, and exposed infrastructure across AWS, Azure, and Google Cloud, finding the critical blind spots that internal compliance tools cannot see.
Moving beyond reactive takedown services, the platform provides preemptive intelligence. By continuously monitoring the deep, dark, and surface web via the DarCache intelligence repository, ThreatNG identifies malicious domain registrations, compromised credentials, and brand impersonation attempts before attacks can be fully mobilized.
Rejecting the delayed, subjective nature of legacy rating agencies, ThreatNG delivers real-time, objective A-F grading across specific exposure vectors. Armed with Legal-Grade Attribution, organizations can confidently challenge inaccurate third-party scores, manage supply chain risk, and prove asset ownership to insurance carriers.
Proprietary Investigation Modules and Correlated Security Metrics
Intelligence Investigation Module
Assessment Scope and Discovered Artifacts
Subdomain enumeration, dangling DNS identification, Web3 domain squatting detection, analysis of missing security headers (HSTS, CSP), and email security validation (SPF/DMARC).
Correlated Security Rating (A - F)
Web Application Hijack Susceptibility, Subdomain Takeover Susceptibility, Cyber Risk Exposure, BEC & Phishing Susceptibility.
Intelligence Investigation Module
Assessment Scope and Discovered Artifacts
Discovery of sanctioned and unsanctioned cloud environments (AWS, Azure, GCP), exposed open cloud buckets, and identification of shadow SaaS implementations across the enterprise.
Correlated Security Rating (A - F)
Data Leak Susceptibility, Supply Chain & Third-Party Exposure, Cyber Risk Exposure.
Intelligence Investigation Module
Assessment Scope and Discovered Artifacts
External identification of exposed API keys, RSA private keys, hardcoded credentials, and open-source repository leaks across development platforms.
Correlated Security Rating (A - F)
Non-Human Identity (NHI) Exposure, Cyber Risk Exposure, Data Leak Susceptibility.
Intelligence Investigation Module
Assessment Scope and Discovered Artifacts
Intelligence repository indexing of compromised credentials, tracking of over 100 specific ransomware group activities, and monitoring of underground forum chatter regarding the target.
Correlated Security Rating (A - F)
Breach & Ransomware Susceptibility, BEC & Phishing Susceptibility, Cyber Risk Exposure.
Intelligence Investigation Module
Assessment Scope and Discovered Artifacts
Proactive monitoring of narrative risk on platforms like Reddit, LinkedIn persona profiling, and extraction of historical data leaks via archived web pages.
Correlated Security Rating (A - F)
Brand Damage Susceptibility, BEC & Phishing Susceptibility, Non-Human Identity (NHI) Exposure.
Intelligence Investigation Module
Assessment Scope and Discovered Artifacts
Monitoring public SEC filings (including 8-K incident disclosures), negative news aggregation, active public lawsuits, and environmental/social governance (ESG) violations.
Correlated Security Rating (A - F)
ESG Exposure, Brand Damage Susceptibility, Data Leak Susceptibility.
Intelligence Investigation Module
Assessment Scope and Discovered Artifacts
Exhaustive, unauthenticated discovery of nearly 4,000 public-facing technologies, encompassing CDNs, WAFs, CRM systems, and DevOps pipelines.
Correlated Security Rating (A - F)
DarChain™
Predicting the Attacker's Next Move
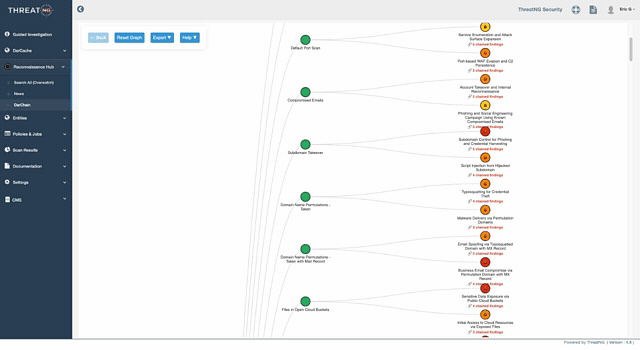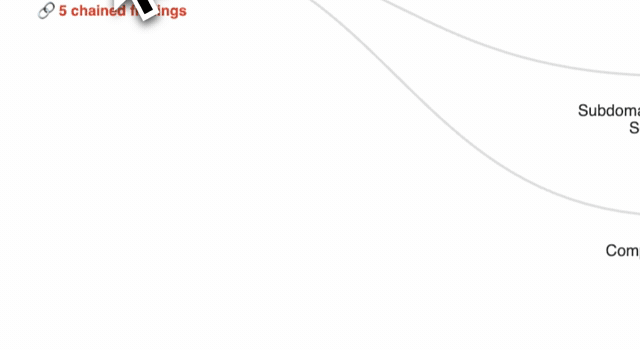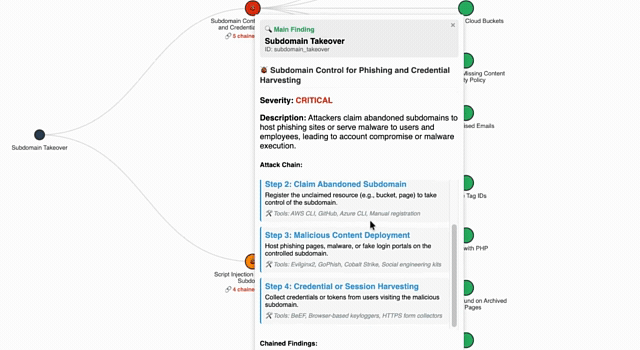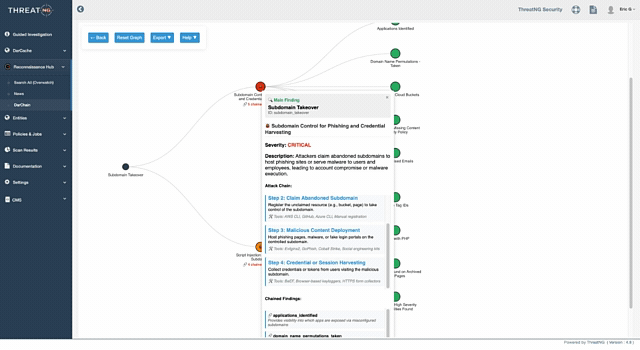
Most security tools hand your team a disconnected list of vulnerabilities, leaving them to guess which ones are actually dangerous. DarChain™ (Digital Attack Risk Contextual Hyper-Analysis Insights Narrative) takes a different approach by automatically mapping the exact sequence of events an adversary will use to breach your organization.
Think of it as tracking the domino effect of a cyberattack: DarChain shows you precisely how a seemingly minor, isolated flaw, such as an abandoned marketing subdomain, can be chained together with a dark web credential leak to launch a devastating, targeted phishing campaign.
By continuously correlating technical, social, and regulatory exposures into a structured threat model, DarChain reveals the specific exploit paths attackers are taking. More importantly, it identifies the critical "Attack Choke Points" in your perimeter, empowering your team to break the adversary's kill chain early, eliminate alert fatigue, and focus remediation exclusively on the vulnerabilities that lead to actual business compromise.
Aligning External Intelligence with Regulatory Mandates
ThreatNG functions not only as a tactical discovery engine but as a strategic GRC instrument. The platform's External GRC Assessment capability provides a continuous, outside-in evaluation of an organization's compliance posture. By identifying exposed assets and digital risks from the perspective of an unauthenticated attacker, the platform maps these findings directly to critical regulatory frameworks, including PCI DSS, HIPAA, GDPR, NIST CSF, ISO 27001, and SOC 2. This ensures that organizations can proactively address external security and compliance gaps before they trigger regulatory scrutiny or mandate costly incident response efforts.
Furthermore, the platform translates raw technical findings into the strategic narrative of adversary behavior via automated MITRE ATT&CK Mapping. By correlating leaked credentials or open ports with specific MITRE techniques, security leaders can prioritize threats based on their actual likelihood of exploitation. This contextual translation provides the empirical business context needed to justify security investments to the boardroom, clearly demonstrating how external exposures affect overall enterprise resilience.

Frequently Asked Questions (FAQ)
-
ThreatNG uses a patented, iterative, and recursive attribute discovery methodology. By analyzing a primary seed, such as a domain name, the platform's Context Filter queries extensive technical, legal, and financial resources. The data extracted from these initial resources is then autonomously utilized to identify additional, hidden attributes, driving a self-expanding discovery loop that uncovers shadow IT and orphaned assets purely from an external, attacker-centric perspective.
-
ThreatNG reduces SOC burnout by automatically correlating isolated technical vulnerabilities with dark web intelligence to prove actual danger. Instead of overwhelming your team with unverified alerts, the Context Engine™ delivers a prioritized blueprint of real attack paths, eliminating the hidden tax of manual investigation.
-
Unlike legacy rating agencies that use delayed, "black box" scoring, ThreatNG provides continuous, transparent, and objective risk assessments. By delivering Legal-Grade Attribution, organizations gain the irrefutable evidence required to challenge inaccurate third-party scores and proactively improve their cyber resilience.
-
ThreatNG replaces static, self-reported vendor questionnaires and delayed "black box" algorithms with continuous, objective assessments. The platform evaluates supply chain exposure by scanning a vendor's cloud environments, technology stack, and dark web presence in real-time. By delivering Legal-Grade Attribution, organizations can accurately quantify third-party risk at scale and challenge inaccurate scores assigned by legacy rating agencies.
-
Yes, ThreatNG consolidates External Attack Surface Management (EASM), Digital Risk Protection (DRP), and Security Ratings into one unified platform. This consolidation eliminates the complexity, integration headaches, and financial burden of managing disjointed vendor dashboards, giving you a single source of truth for external risk.
-
Yes, by providing superior contextual relevance. While traditional threat intelligence feeds deliver global, macroeconomic threat data that often amounts to generic noise, ThreatNG provides personalized intelligence. Features such as the Reconnaissance Hub and the DarCache repository integrate curated threat data directly with an organization's specific vulnerabilities, ensuring security teams only review intelligence that matches their verified external assets.
-
ThreatNG is completely frictionless and requires zero internal agents, credentials, or API connectors to operate. It performs unauthenticated, outside-in discovery to map your external attack surface exactly as an adversary sees it, delivering immediate value without adding administrative overhead to your IT team.
-
ThreatNG translates technical findings into clear, business-centric metrics by mapping exposures directly to regulatory frameworks and MITRE ATT&CK techniques. This empowers CISOs with the objective data and contextual certainty needed to effectively communicate cyber risk, justify security budgets, and demonstrate operational resilience to the board.
-
The Context Engine™ is a proprietary solution that achieves Irrefutable Attribution through multi-source data fusion. It iteratively correlates external technical security findings with decisive legal, financial, and operational context. This eliminates the guesswork and false positives that plague traditional EASM tools, ending the "Crisis of Context" and removing the hidden tax on the SOC by providing a precise, prioritized operational mandate for remediation.