External PCI Assessment
Mastering PCI DSS v4.0: Continuous Compliance for Organizations, QSAs, ASVs, and Consultants
Organizations that need to comply with PCI DSS, along with Qualified Security Assessors (QSAs), Approved Scanning Vendors (ASVs), and PCI DSS consulting firms, face new challenges with the Payment Card Industry Data Security Standard (PCI DSS) v4.0. This update transforms compliance from an annual audit to a continuous security requirement. All of these groups must identify elusive external risks, manage dynamic attack surfaces, and ensure continuous validation.
ThreatNG offers a revolutionary approach, providing an attacker's perspective to uncover the "unknown unknowns" that traditional methods miss. This empowers organizations and their compliance partners to achieve and maintain robust PCI DSS compliance.
The PCI DSS Maze: Challenges Faced by Organizations and Their Compliance Partners
PCI DSS v4.0 introduces 64 new requirements and over 100 changes, making compliance more challenging than ever. Organizations and their partners are grappling with critical pain points:
Organizations (Merchants and Service Providers)
Managing Third-Party & Supply Chain Risk: PCI DSS v4.0 places full liability on merchants for third-party security incidents (Requirement 12.8.x), making continuous oversight of vendors critical yet challenging.
Supporting Continuous Compliance: Moving beyond one-time compliance projects to ongoing security posture management requires continuous data and insights.
Integrating Disparate Security Data: Synthesizing information from various security tools for a holistic compliance view is complex and resource-intensive.
Incomplete Scope Definition: Struggling to identify all systems that interact with or could impact the Cardholder Data Environment (CDE), including "shadow IT" and forgotten assets. PCI DSS v4.0 Requirement 12.5.2 mandates annual scope validation, increasing this burden.
Qualified Security Assessors (QSAs)
Incomplete Scope Definition: QSAs struggle to identify all systems that interact with or could impact the CDE, including "shadow IT" and forgotten assets. PCI DSS v4.0 Requirement 12.5.2 mandates annual scope validation, increasing this burden.
Evidence Collection Burden: Gathering detailed evidence for comprehensive Reports on Compliance (RoCs) is time-consuming and complex.
Point-in-Time vs. Continuous Compliance: Traditional annual audits do not provide continuous assurance, leading to degradation of security controls between assessments.
Generic Remediation Guidance: Providing precise, prioritized remediation advice for complex external vulnerabilities can be challenging.
Approved Scanning Vendors (ASVs)
Limited External Visibility: ASV scans provide a snapshot of known external vulnerabilities (PCI DSS 11.3.2) but often miss broader digital risks like phishing infrastructure, data leaks, or sensitive code exposure.
False Positives & Remediation Validation: Managing false positives and ensuring comprehensive rescans after remediation can be a time-consuming back-and-forth.
Meeting PCI DSS 11.3.2.1: The new requirement for external vulnerability scans after significant system modifications adds pressure for continuous, accurate scanning.
PCI DSS Consulting Firms
Accelerating Gap Assessments: Quickly identifying all compliance gaps, especially those stemming from external exposures or third-party dependencies, is a significant hurdle.
Managing Third-Party & Supply Chain Risk: PCI DSS v4.0 places full liability on merchants for third-party security incidents (Requirement 12.8.x), making continuous oversight of vendors critical yet challenging.
Integrating Disparate Security Data: Synthesizing information from various security tools for a holistic compliance view is complex and resource-intensive.
Supporting Continuous Compliance: Guiding clients beyond one-time compliance projects to ongoing security posture management requires continuous data and insights.

ThreatNG: Your Strategic Advantage in PCI DSS Compliance
ThreatNG is an all-in-one External Attack Surface Management (EASM), Digital Risk Protection (DRP), and Security Ratings solution, purpose-built to address the evolving demands of PCI DSS v4.0.
How ThreatNG Solves Your PCI DSS Challenges:
We offer an entirely external, unauthenticated discovery that mimics an attacker's view, exposing vulnerabilities and exposures that internal tools and traditional scans often overlook. By continuously monitoring your external attack surface, digital risk, and security ratings, ThreatNG provides you with real-time intelligence to stay compliant throughout the year.
Problem
Incomplete Scope Definition (Organizations, QSAs, Consultants)
ThreatNG Solution
Uncovers unknown or "shadow IT" assets that fall into the PCI DSS scope or the "connected-to scope".
Capability & Benefit
External Discovery: Purely external, unauthenticated discovery using no connectors. Identifies orphaned subdomains, exposed developer environments, mobile applications, and online sharing exposures.
Problem
Point-in-Time vs. Continuous Compliance (All)
ThreatNG Solution
Enables a shift from periodic checks to proactive, continuous compliance management, aligning with the core intent of PCI DSS v4.0.
Capability & Benefit
Continuous Monitoring: Ongoing observation of external attack surface, digital risk, and security ratings.
External GRC Assessment: Continuous, outside-in evaluation mapping findings directly to PCI DSS.
Problem
Limited External Visibility (Organizations, ASVs)
ThreatNG Solution
Provides a deeper, attacker-centric view of external risks beyond basic vulnerability scans.
Capability & Benefit
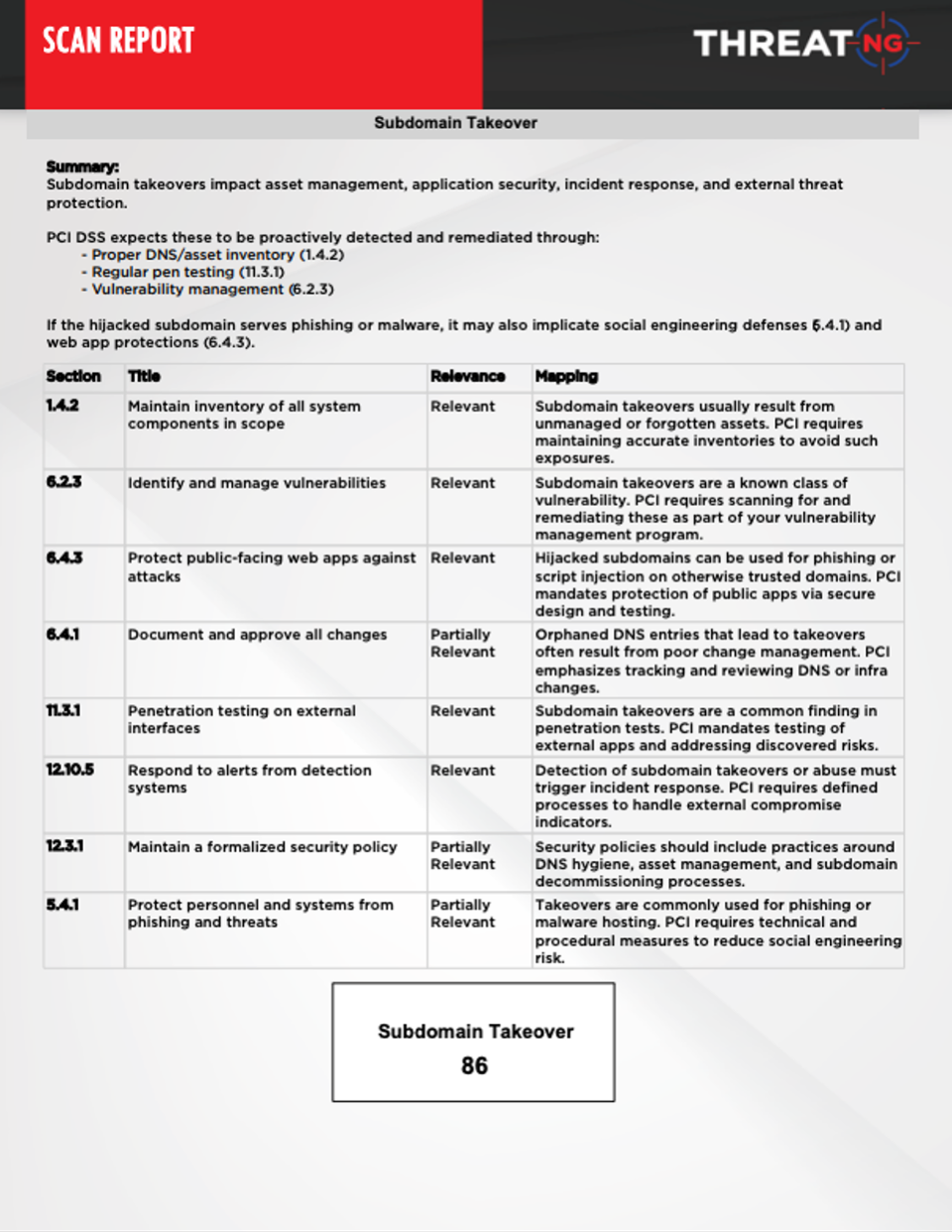
Subdomain Takeover Susceptibility: Identifies vulnerable subdomains that could be exploited for phishing or malware attacks.
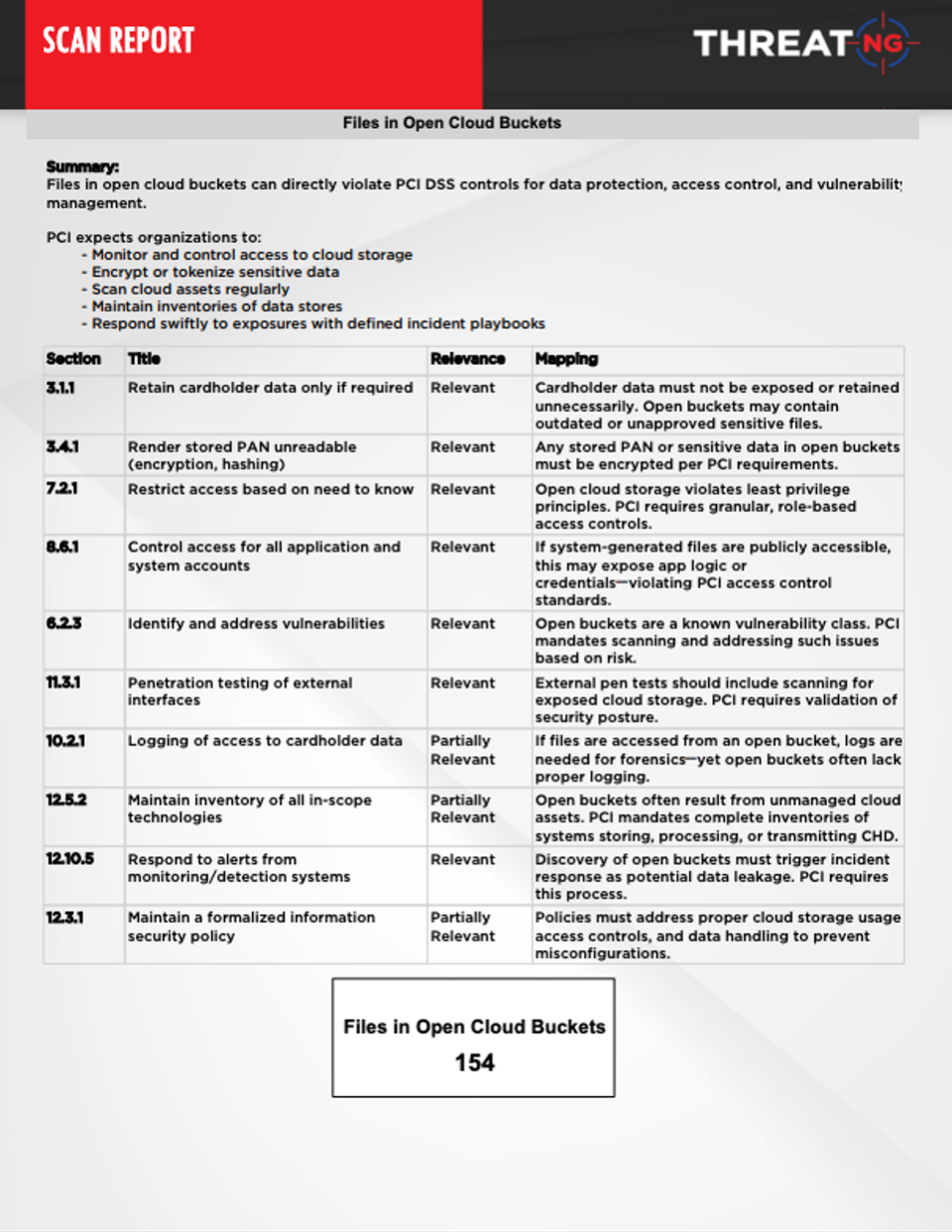
Files in Open Cloud Buckets: Detects publicly exposed sensitive files in cloud storage.
Sensitive Code Exposure: Discovers sensitive data (e.g., API keys, credentials) in public code repositories.
BEC & Phishing Susceptibility: Assesses vulnerability to business email compromise and phishing attacks.
Problem
Managing Third-Party & Supply Chain Risk (Organizations, Consultants, QSAs)
ThreatNG Solution
Offers crucial external visibility into vendor attack surfaces, supporting due diligence and continuous monitoring of third-party compliance.
Capability & Benefit
Supply Chain & Third Party Exposure: Derived from domain intelligence, technology stack, and cloud/SaaS exposure of vendors.
Problem
Generic Remediation Guidance (Organizations, QSAs, Consultants)
ThreatNG Solution
Provides precise, prioritized, and actionable advice for identified risks.
Capability & Benefit
Knowledgebase: Embedded with risk levels, reasoning, recommendations, and reference links.
Intelligence Repositories (DarCache): Provides real-world exploitability context (EPSS, KEV, PoC exploits) for vulnerabilities.
Problem
Evidence Collection Burden (Organizations, QSAs)
ThreatNG Solution
Automates and centralizes the gathering of external evidence, reducing manual effort.
Capability & Benefit
Reporting: Offers Executive, Technical, and External GRC Assessment Mappings (e.g., PCI DSS) reports.
Collaboration and Management: Includes dynamically generated Correlation Evidence Questionnaires.
Clear PCI DSS Alignment Through Actionable External Assessments
ThreatNG streamlines your external PCI assessment by providing clear, actionable insights into your security posture from an attacker's perspective. Our easy-to-read reports detail crucial findings, including sensitive information exposed in public repositories, compromised credentials, default port scans, and mentions on the dark web. Each finding is meticulously mapped to relevant PCI DSS requirements, enabling organizations to understand their compliance status and prioritize remediation efforts to enhance their security defenses and protect cardholder data.

What Makes ThreatNG Uniquely Powerful?
The True Attacker's Perspective: Unlike internal tools or limited external scans, ThreatNG performs purely external, unauthenticated discovery. This means we see your digital footprint exactly as an adversary would, identifying blind spots before they become breaches.
Continuous, Holistic Intelligence: We move beyond point-in-time assessments. ThreatNG provides continuous monitoring across your entire external attack surface, digital risk, and security ratings, ensuring you're always aware of emerging threats and compliance gaps.
Actionable, Prioritized Insights: Our Knowledgebase and DarCache Intelligence Repositories don't just list vulnerabilities; they provide context, reasoning, and recommendations, including exploitability likelihood (EPSS) and actively exploited vulnerabilities (KEV). This empowers you to prioritize remediation efforts effectively, aligning with PCI DSS v4.0's Targeted Risk Analysis (12.3.1).
Direct PCI DSS Alignment: ThreatNG's External GRC Assessment capability maps findings directly to PCI DSS requirements, providing clear, auditable evidence of your external security posture. This streamlines compliance efforts and reduces audit stress.
Empowering Partnerships: ThreatNG is designed to be a force multiplier for organizations, QSAs, ASVs, and consulting firms. We enhance your existing services, enable new offerings, and help you deliver superior value to your clients, fostering stronger, long-term relationships and new revenue streams.
Ready to Future-Proof Your PCI DSS Compliance?
Don't let hidden external risks jeopardize your PCI DSS compliance, incur hefty fines, or damage your reputation. ThreatNG provides the continuous, attacker-centric visibility you need to identify, prioritize, and proactively remediate external threats. Take the first step towards a more secure and compliant future.
Frequently Asked Questions
This FAQ addresses common questions about ThreatNG Security's role in enhancing PCI DSS compliance, highlighting its unique external perspective and continuous monitoring capabilities.
-
Traditionally, PCI DSS compliance has often relied on a "point-in-time" assessment model, primarily focusing on internal network scans and manual evidence collection. Organizations would prepare for annual audits, often overlooking the continuous nature of risk and the vulnerabilities lurking outside their perimeter. This approach often created an incomplete security posture, as external and unknown assets, third-party risks, and evolving digital threats were not consistently monitored from an attacker's perspective. Internal tools would miss issues like subdomain takeovers, exposed cloud buckets, or leaked credentials that attackers could use to breach the Cardholder Data Environment (CDE).
-
ThreatNG Security provides a crucial external, attacker-centric view of an organization's digital footprint, which is often a blind spot in traditional PCI DSS compliance efforts. Its significance lies in its ability to:
Proactively identify external risks: Uncover unknown or forgotten assets, misconfigurations, and vulnerabilities before they can be exploited by attackers.
Enable continuous compliance: Shift from a reactive, point-in-time approach to proactive, continuous monitoring, aligning with PCI DSS v4.0's emphasis on ongoing security.
Provide an outside-in perspective: Simulate how an attacker would view and target an organization's external attack surface, identifying critical weaknesses that internal scans might miss.
-
The direct mapping of ThreatNG's external findings to specific PCI DSS requirements is highly significant because it:
Provides actionable intelligence: Each external finding (e.g., "Subdomain Takeover Susceptibility," "Files in Open Cloud Buckets," "APIs on Subdomains," "Compromised Emails," "Exposed Sensitive Information in Public Repositories") is directly linked to relevant PCI DSS sections (e.g., Requirement 2: Secure configurations, Requirement 6: Secure systems and software, Requirement 8: Access control, Requirement 10: Logging and monitoring, Requirement 12: Information security policy).
Streamlines compliance efforts: Organizations can see precisely how external vulnerabilities impact their compliance posture, allowing for prioritized remediation efforts.
Facilitates audit readiness: The explicit mapping provides clear evidence of addressing PCI DSS requirements from an external security standpoint, aiding QSAs in their assessments. For instance, discovering "Subdomains Missing Content Security Policy" directly relates to PCI DSS Requirement 6.4 (Public-Facing Web Applications) by identifying missing security controls.
-
ThreatNG's approach is essential for PCI DSS compliance because it directly addresses critical gaps that can lead to data breaches and penalties for non-compliance. Its importance stems from:
Breach Prevention: By identifying and helping remediate external attack vectors, ThreatNG significantly reduces the likelihood of a PCI-related data breach.
Penalty Avoidance: Non-compliance with PCI DSS can result in severe fines, loss of card processing privileges, and reputational damage. ThreatNG helps proactively mitigate these risks.
PCI DSS v4.0 Readiness: The new version of PCI DSS (v4.0) mandates a stronger focus on continuous compliance, customized approaches based on risk, and enhanced security for e-commerce and third-party relationships. ThreatNG's continuous external monitoring capabilities are crucial for meeting these evolving requirements.
-
PCI DSS compliance affects any organization that stores, processes, or transmits cardholder data. This includes:
Merchants: Businesses of all sizes, from small e-commerce shops to large retailers.
Service Providers: Organizations that manage or provide services impacting cardholder data environments, such as payment processors, managed hosting providers, and third-party IT vendors.
ThreatNG is essential to a wide range of stakeholders within these organizations:
CISOs/Security Leadership: For a comprehensive view of external risk and to demonstrate due diligence.
Compliance Officers: To ensure continuous adherence to PCI DSS v4.0 requirements and simplify audit preparation.
IT Security Teams: To prioritize and remediate externally exposed vulnerabilities.
Risk Management Teams: To accurately assess external digital risks, including third-party exposure.
Developers: To identify and fix code-related vulnerabilities visible externally.
Legal Teams: To mitigate potential liability from data breaches.
-
ThreatNG's differentiated approach is characterized by:
Purely External, Unauthenticated Discovery: Unlike internal scanners, ThreatNG operates from an attacker's perspective, without requiring agents, network access, or credentials. It identifies digital assets and vulnerabilities that are exposed to the internet, including those unknown to the organization (shadow IT).
Comprehensive External Attack Surface Management (EASM): It maps the entire external digital footprint, including forgotten subdomains, exposed cloud buckets, misconfigured APIs, and more.
Digital Risk Protection (DRP): It goes beyond technical vulnerabilities to identify non-technical risks such as compromised credentials on the dark web, phishing susceptibility, and brand impersonations.
Continuous Monitoring: ThreatNG provides real-time visibility into changes in the external attack surface and digital risk posture, ensuring ongoing compliance and security, rather than relying on periodic snapshots.
-
ThreatNG solves several critical problems related to PCI DSS compliance:
Incomplete Scope Definition: It helps identify unknown and forgotten internet-facing assets that fall within the "connected-to" PCI scope, preventing hidden vulnerabilities.
Third-Party Risk Management: ThreatNG provides external visibility into the security posture of third-party vendors and service providers handling cardholder data, addressing a significant area of increased scrutiny in PCI DSS v4.0.
Detection of External Digital Risks: It uncovers vulnerabilities like subdomain takeovers, exposed sensitive information in public repositories (e.g., GitHub), and compromised emails that can lead to cardholder data breaches.
Maintaining Continuous Compliance: ThreatNG helps organizations move beyond static audits by providing continuous monitoring and actionable intelligence, enabling them to maintain a strong security posture throughout the year.
E-commerce Security: Identifies external vulnerabilities specific to e-commerce environments, crucial for PCI DSS v4.0's new requirements for protecting payment pages.
-
ThreatNG is highly complementary to existing PCI compliance solutions and processes:
Complements Internal Vulnerability Scanners: While internal scanners focus on the network perimeter and internal systems, ThreatNG provides the crucial external view, identifying vulnerabilities from an attacker's perspective that internal tools might miss.
Enhances QSA Audits: QSAs can use ThreatNG's external assessment findings and continuous monitoring reports as valuable evidence during their audits, streamlining the assessment process and providing a more comprehensive view of the organization's security posture. ThreatNG's detailed mappings to PCI DSS requirements directly aid QSAs in their evidence collection.
Augments ASV Scans: ThreatNG's External Attack Surface Management (EASM) and Digital Risk Protection (DRP) capabilities offer deeper context and insights beyond what Approved Scanning Vendors (ASVs) typically provide in their quarterly external vulnerability scans. ThreatNG can help identify the root causes of potential ASV findings or uncover issues that a standard scan might not detect.
Supports Security Operations Centers (SOCs): The continuous flow of external risk intelligence from ThreatNG can feed into an organization's SOC, enabling more proactive threat hunting and incident response related to externally exposed assets.
Integrates with GRC Platforms: The structured assessment findings and PCI DSS mappings can be integrated into GRC (Governance, Risk, and Compliance) platforms, providing a holistic view of compliance status.
By filling the external blind spot and providing continuous, attacker-centric insights, ThreatNG ensures a more robust and complete PCI DSS compliance program, working in synergy with an organization's existing security investments.